SDwan cloud interconnection
To address the current challenges faced by enterprise networks such as expensive dedicated line cost, complex operation management, difficulty in ensuring business experience, and weak WAN security construction, MUCSE RSP series chips fully support the national secret IPSEC VPN technical specifications, including the national secret algorithm interface invocation, key negotiation, encrypted communication, etc.;The chip also supports algorithm registration to the system and system encryption framework invocation. The chip adopts a reconfigurable architecture and supports private algorithms, private protocols and customized business logic.
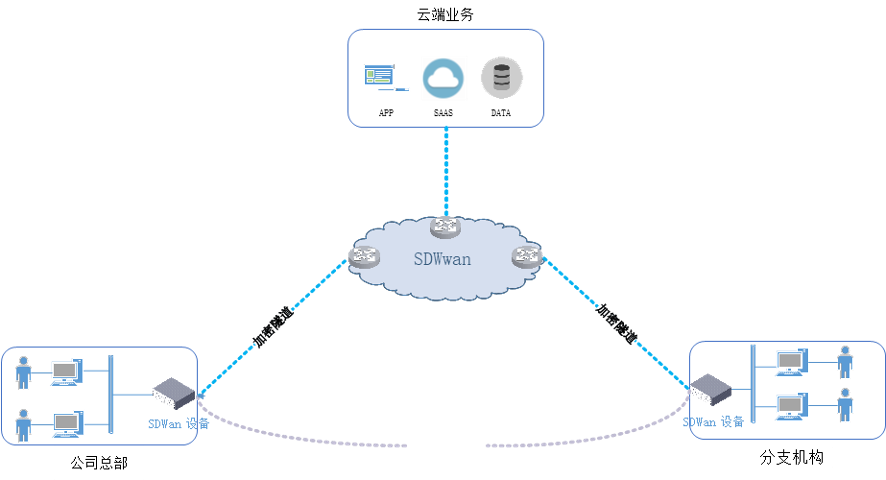
Schematic diagram of the SDWan network topology
• Users can access the Internet through SD-WAN devices.
•When users transmit sensitive information, SD-WAN devices can protect data by establishing encrypted tunnels.
• Accessing cloud resources is also protected by encrypted tunnels.

Schematic diagram of the network attack
• Eavesdropping means that hackers can access the network of business communication in a "sideways" manner and view the communication data without being discovered.
• Business flow analysis refers to obtaining complete business communication interaction data based on eavesdropping on business data to enable business analysis.
• Message tampering refers to modifying critical information in the business communication data based on business flow analysis.
• Impersonation refers to inserting messages into the network in a forged identity manner based on business flow analysis.
• Non-repudiation refers to the situation where the legitimacy of the data cannot be authenticated, and both the sender and receiver are unable to confirm if the message was sent by the other
party.
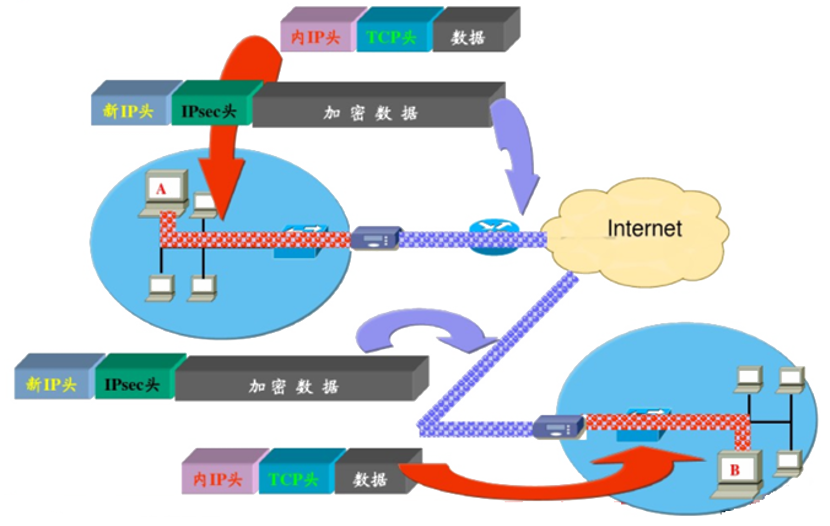
Work diagram of the IPSec VPN technology encryption tunnel
• Hide original data information by encrypting data
• Prevent replay attacks with sliding windows
• Ensure data integrity through HMAC message authentication code
• Through security indexing ensures that data between tunnels will not interfere with each other